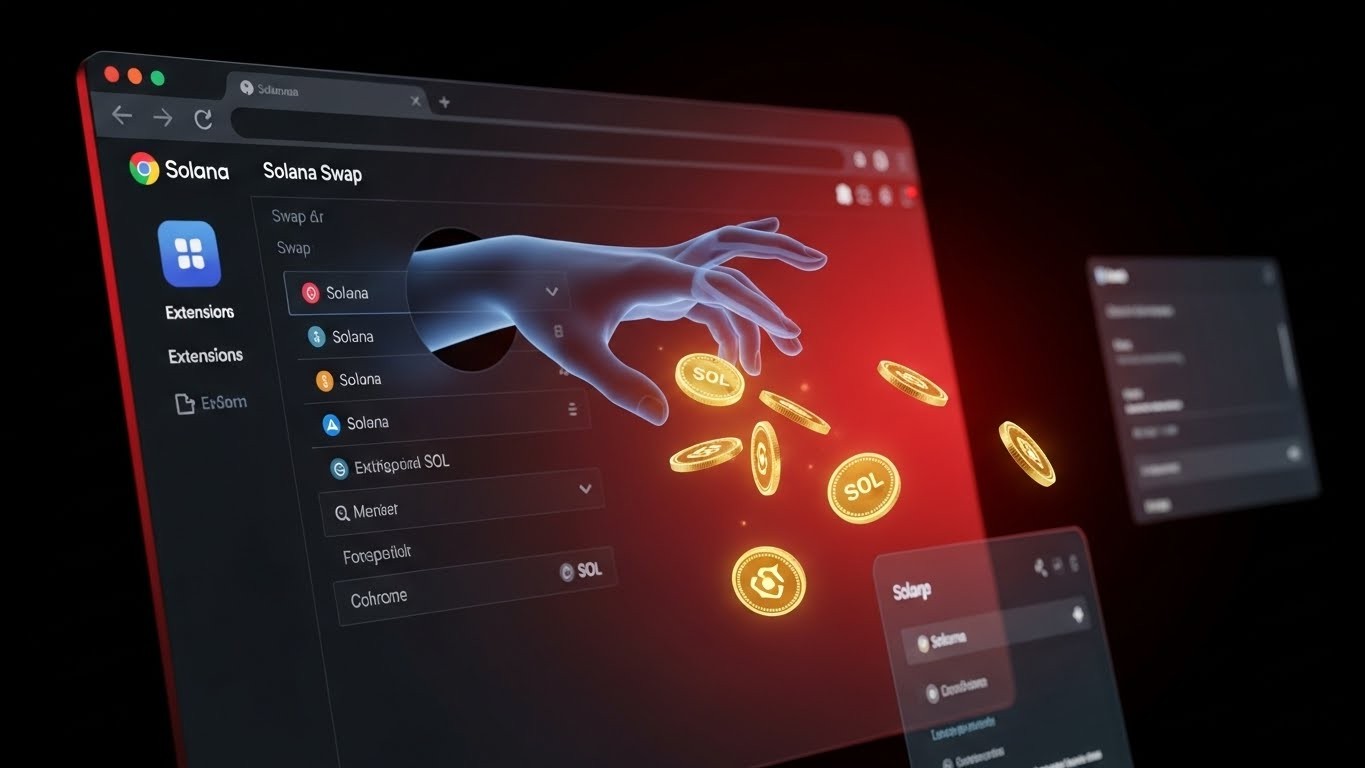
I still remember the first time I installed a shiny new crypto browser extension that promised to make my life easier. One click and boom—swap tokens right from Twitter. Sounded like magic. Turns out, for a lot of Solana users lately, that “magic came with a nasty little catch.
A Chrome extension calling itself Crypto Copilot has been quietly skimming funds from anyone who used it to trade on Solana. Not some massive hack, not a phishing site—just a seemingly legitimate tool that slipped through the Chrome Web Store and started helping itself to a cut of every single swap.
The Silent 0.05% Tax Nobody Asked For
Here’s the scary part: the theft was practically invisible.
When you clicked “swap” inside Crypto Copilot, the extension built what looked like a perfectly normal Raydium transaction. You saw the usual confirmation screen, hit approve in your wallet, and the trade went through. What you didn’t see was the extra line of code tucked inside that same transaction: a tiny SystemProgram.transfer instruction that sent at least 0.0013 SOL (or 0.05% of the trade, whichever was bigger) straight to the attacker’s wallet.
Because everything happened in a single atomic transaction, the diversion was impossible to stop once you signed. Your wallet showed one transaction, the blockchain recorded one transaction, but two transfers actually happened. Genius in its simplicity, terrifying in its effectiveness.
“The user only ever sees the swap. The hidden transfer is buried in the middle of the instructions and never displayed in the confirmation UI most wallets show.”
Security researcher who analyzed the code
How the Trick Actually Worked Under the Hood
Let me break it down without getting too much jargon.
- You connect your Solana wallet (Phantom, Solflare, whatever) to the extension.
- You browse X/Twitter and see a token you want to buy.
- Crypto Copilot builds a transaction that routes through Raydium for the real swap.
- Right before the final instruction, it inserts an extra one: “transfer X SOL to this random address”.
- The whole package gets sent to your wallet as a single transaction.
- You approve what looks like a normal swap.
- The attacker gets paid. Every. Single. Time.
The code was deliberately obfuscated—minified, variables renamed to gibberish, strings encrypted—so casual inspection wouldn’t raise red flags. The extension even phoned home to a Vercel dashboard that tracked wallets and referral stats. Classic scammer infrastructure dressed up as a real product.
Why Didn’t More People Notice Sooner?
Two reasons.
First, the amounts were tiny on small trades. Losing 0.002 SOL here and there feels like slippage or fees. Most people blame Jupiter or Raydium routing instead of suspecting their brand-new “copilot”.
Second, very few retail users actually expand the “view instructions” section in their wallet before signing. I’m guilty of this too—when you’re sniping ten memes a day, you get lazy. That laziness is exactly what these attackers count on.
Only power users who simulate every transaction (or security researchers with too much free time) caught the hidden transfer.
The Bigger Picture Nobody Wants to Talk About
This isn’t an isolated incident. It’s the latest chapter in a very long book titled “Browser Extensions Are the New Phishing Pages”.
We’ve seen fake MetaMask extensions, fake Keplr extensions, fake TronLink—you name it. The pattern is always the same:
- Promise something incredibly convenient.
- Get listed on the official store (yes, really).
- Wait for victims to hand over full signing rights.
- Start slow-draining or wait for a big transaction to empty the wallet completely.
In my opinion, the Chrome Web Store’s review process for crypto extensions is still playing catch-up. Until Google starts requiring open-source code or mandatory third-party audits for anything that touches private keys, these incidents will keep happening.
How to Actually Protect Yourself in 2025
Practical, no-BS advice I give to every friend who asks:
- Use a dedicated “hot” wallet for DeFi gambling with only the money you’re willing to lose.
- Never give unlimited token approvals—revoke them regularly on sites like revok.cash.
- Simulate every transaction you don’t 100% trust. Tools like SolanaFM or Solscan let you preview what will happen before signing.
- Stick to extensions with public GitHub repos and thousands of reviews—or better yet, use dApp websites directly.
- Turn on transaction simulation in Phantom (it’s off by default for some reason) and actually read the warnings.
- If something promises “trade from Twitter”—run. Real convenience usually comes with real risk.
I know that sounds paranoid, but I’ve watched too many people lose five-figure bags because they wanted to save thirty seconds.
What Happens Next for Crypto Copilot Victims?
Unfortunately, the stolen SOL is almost certainly gone for good. The attacker’s wallet has been draining to mixers and exchanges for months. On-chain recovery is basically impossible once funds are bridged or tumbled.
The extension has been pulled from the Chrome store (finally), but copies are almost certainly floating around on sketchy download sites. If you ever installed something called Crypto Copilot, uninstall it immediately and check your transaction history for unexpected transfers.
The silver lining? Incidents like this push the ecosystem to get better. Wallets are starting to highlight hidden transfers more aggressively. Simulation tools are becoming default-on. And hopefully Google tightens the screws on crypto extensions before the next “copilot” shows up.
Look, I love the convenience of browser extensions as much as anyone. But every time we hand over signing capability to a random developer for the sake of a smoother UX, we’re rolling the dice.
Crypto Copilot wasn’t the first to abuse that trust, and it won’t be the last. The only real defense is staying a little paranoid, simulating everything, and remembering the oldest rule in crypto:
If it looks too convenient to be safe, it probably is.
Stay sharp out there.