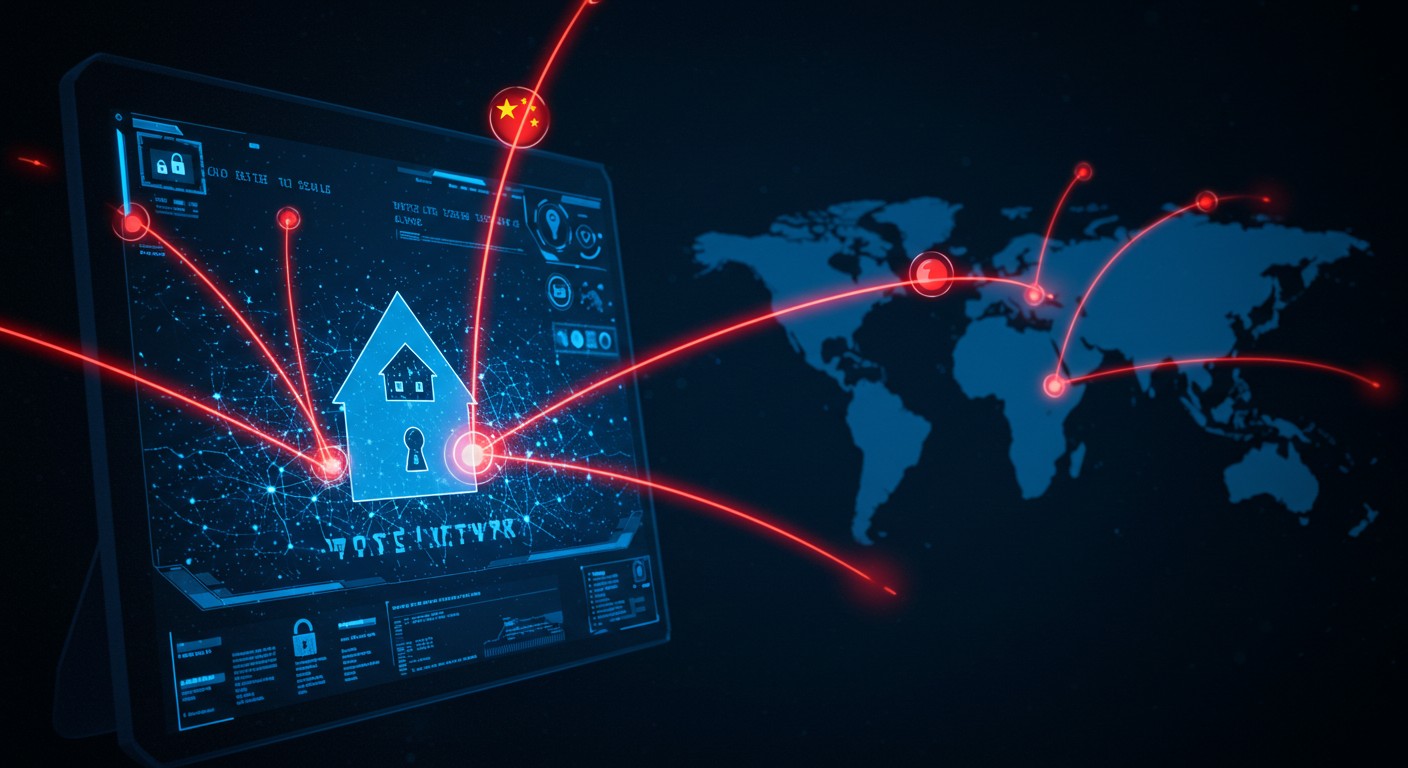
Imagine waking up to find your local water supply compromised—not by a natural disaster, but by an invisible enemy thousands of miles away. That’s the chilling reality one California water utility faced when it detected over 6 million connection attempts from China-based servers in just a single week. It’s a stark reminder that our critical infrastructure—the systems we rely on daily—is under constant threat in today’s digital age. This isn’t just a tech issue; it’s a wake-up call about the vulnerabilities lurking in the networks that keep our society running.
The Growing Threat to Critical Infrastructure
In a world where everything from our water to our power grids depends on interconnected systems, the rise of cyberattacks feels like a plot twist no one saw coming. The South Coast Water District, serving roughly 40,000 residents in Orange County, California, recently shared a jaw-dropping statistic: their network blocked 6 million connection attempts from China in just seven days. That’s not a typo. According to industry experts, this barrage of hits is part of a broader effort by foreign actors to probe for weaknesses in America’s essential services.
Why water utilities? They’re a lifeline. Disrupt them, and you disrupt daily life—drinking water, sanitation, even firefighting capabilities. Yet, many of these systems, especially in smaller districts, weren’t built with cybersecurity as a top priority. I’ve always found it a bit unsettling how much we take these systems for granted, assuming they’ll always work flawlessly. But when a single utility faces millions of probes in a week, it’s clear the stakes are higher than ever.
What’s Behind the Attacks?
The sheer volume of these connection attempts points to a calculated strategy. Cybersecurity experts suggest these are likely reconnaissance missions—hackers scanning for vulnerabilities they can exploit later. Think of it like a burglar rattling every door in a neighborhood to see which one’s unlocked. In this case, the culprits are believed to be state-backed groups, with China frequently named as a top player in this shadowy game.
If you’re running a water utility in California, you probably don’t have customers in China. So why are their servers knocking on your digital door?
– Cybersecurity expert during an industry webinar
The answer lies in the broader context of geopolitical tensions. Intelligence reports have flagged campaigns like Volt Typhoon, a Chinese state-backed operation designed to infiltrate and potentially disrupt critical U.S. infrastructure. The goal? To create chaos in the event of a conflict. It’s not just water systems either—telecoms, government agencies, and even nuclear programs have been targeted. Perhaps the most alarming part is how these attacks exploit known vulnerabilities in widely used software, catching smaller utilities off guard.
Why Water Systems Are Vulnerable
Water utilities, especially smaller ones, are often sitting ducks. Many were designed for reliability and remote access, not to fend off sophisticated cyberattacks. Picture a rural water pump station in rugged terrain—its network might prioritize uptime over security. Add to that the fact that smaller districts often lack the budget or expertise to implement robust cyber defenses, and you’ve got a recipe for trouble.
- Limited Resources: Smaller utilities can’t afford top-tier cybersecurity teams.
- Outdated Systems: Legacy infrastructure often runs on software with known vulnerabilities.
- Remote Access Needs: Systems built for convenience can be entry points for hackers.
In 2024, a major U.S. water utility fell victim to a cyberattack, proving that even large players aren’t immune. But it’s the smaller systems, like the one in Massachusetts hit by Volt Typhoon in 2023, that highlight the widespread risk. These incidents aren’t isolated—they’re part of a pattern that’s been growing for years.
The Scale of the Problem
The California utility’s experience isn’t unique. Their firewall dashboard also revealed over 34,000 blocked attempts from Bulgaria and 21,000 from Iran in the same week. These numbers are staggering, but they’re just a snapshot of a global issue. Cybersecurity researchers have uncovered a troubling trend: foreign actors, particularly from China, are systematically studying Western infrastructure for weaknesses.
One study found over 360 Chinese academic papers focused on U.S. power grids, with another 160 targeting European systems. These papers often dive deep into failures and vulnerabilities, raising questions about their true purpose. Are they purely academic, or are they laying the groundwork for something more sinister? In my view, the sheer volume of this research feels like more than just scholarly curiosity.
| Country of Origin | Connection Attempts | Target |
| China | 6,000,000+ | California Water Utility |
| Bulgaria | 34,000+ | California Water Utility |
| Iran | 21,000+ | California Water Utility |
These figures paint a picture of relentless probing. It’s not just water systems—Chinese hackers have targeted everything from telecom networks to government agencies. A recent report highlighted a state National Guard network being heavily compromised in 2024, showing how no sector is off-limits.
How Are Utilities Fighting Back?
Thankfully, the California utility in question had a robust firewall in place, blocking those millions of connection attempts. But not every system is so well-equipped. Industry webinars, like the one hosted by a water sector group, are pushing for better defenses. Experts recommend tailoring access controls—basically, locking the digital doors to anyone who doesn’t need to be there.
Limit access to your servers. If you don’t have customers in certain regions, block those connections outright.
– Cybersecurity professional
This advice sounds simple, but implementing it across sprawling, often outdated networks is no small feat. Some utilities are turning to advanced firewall dashboards that provide real-time insights into threats. Others are leaning on federal mandates, like the 2022 legislation requiring critical infrastructure to report cyber incidents within 72 hours. Task forces are also stepping in, helping smaller utilities shore up their defenses.
- Upgrade Firewalls: Invest in systems that can detect and block suspicious traffic.
- Train Staff: Educate employees on recognizing phishing and other cyber threats.
- Patch Software: Regularly update systems to close known vulnerabilities.
But here’s the kicker: even with these measures, the threat evolves faster than many utilities can keep up. Hackers exploit vulnerabilities in widely used software, like the recent Microsoft SharePoint breach, to gain access to entire networks. It’s a cat-and-mouse game, and the stakes couldn’t be higher.
The Bigger Picture: A Global Cyber Threat
While China’s role in these attacks grabs headlines, they’re not alone. Campaigns like Salt Typhoon and Linen Typhoon show how coordinated these efforts are, targeting everything from political figures to nuclear programs. In one case, hackers exploited a Cisco vulnerability to target 1,000 devices globally in just a month. Another breach saw over 400 systems compromised through a single software flaw.
What’s particularly unnerving is how these attacks exploit known vulnerabilities. It’s like leaving your car unlocked in a bad neighborhood and being surprised when it gets stolen. Cybersecurity experts warn that the rapid adoption of these exploits means hackers are always one step ahead. For utilities, this means constant vigilance is non-negotiable.
What Can We Do About It?
So, where do we go from here? For starters, awareness is key. The more we understand the scope of these threats, the better equipped we are to demand action. I’ve always believed that public pressure can push policymakers to prioritize cybersecurity funding for critical infrastructure. Smaller utilities need grants and support to bolster their defenses—otherwise, they’re left fighting a losing battle.
Individually, we can also play a role. Supporting local utilities by advocating for stronger cybersecurity measures or even reporting suspicious activity can make a difference. It’s not just about water—it’s about the systems that keep our communities alive.
Cybersecurity Checklist for Utilities: - Monitor network traffic in real-time - Restrict access to essential personnel - Update software patches regularly - Train staff on cyber threat awareness
Perhaps the most sobering takeaway is that these attacks aren’t going away. If anything, they’re ramping up. The California utility’s experience is a glimpse into a broader, more troubling trend—one that demands our attention before it’s too late.
Final Thoughts: A Call to Action
The 6 million connection attempts on a single water utility are more than a statistic—they’re a warning. Our critical infrastructure is under siege, and the consequences of inaction could be catastrophic. From upgrading firewalls to pushing for federal support, there’s a lot we can do to fight back. But it starts with recognizing the threat for what it is: a clear and present danger to the systems we can’t live without.
In my experience, it’s easy to brush off cybersecurity as someone else’s problem—until it’s not. The next time you turn on the tap, think about what it takes to keep that water flowing. And then ask yourself: are we doing enough to protect it?